AuraQ has vast experience helping organisations find the gaps that can be filled to enhance their business. This could be to improve efficiency, integrate legacy systems or deliver new portals and strategic applications to create competitive advantage. Contact us to request a free, no obligation Gap Analysis.
5 ways in which Mendix supports cyber security principles
As a current Masters student in Cyber Security, I am constantly exposed to the threats we face both as developers and consumers in addition to the best way to mitigate these threats. A major flaw in some companies is that security is treated as an afterthought – resulting in inadequate security measures being built on top of finished products. The dangers of weak security shouldn’t be underestimated – IBM concluded in 2022 that the average cost of a data breach is $4.35 million, and that 60% of all data breaches surveyed resulted in increased costs to customers. To reduce the risk of data breaches, security must be built into the functionality of products.
During development, it is crucial to be security conscious to reduce the risk of vulnerabilities existing at the point of deployment. This can be a particularly daunting task when developing with programming languages, where insecure coding practices can result in breaches through vulnerabilities such as SQL injection and buffer overflows. Fortunately, Mendix’s low-code platform reduces the risk of vulnerable applications by integrating security principles into the core of development. This is highlighted by their implementation of ISO 27001 in their platform, showing that information security is a key concern for Mendix throughout development. This article looks at some vital cyber security principles and how Mendix supports applications to achieve these.
1. Fail-safe defaults
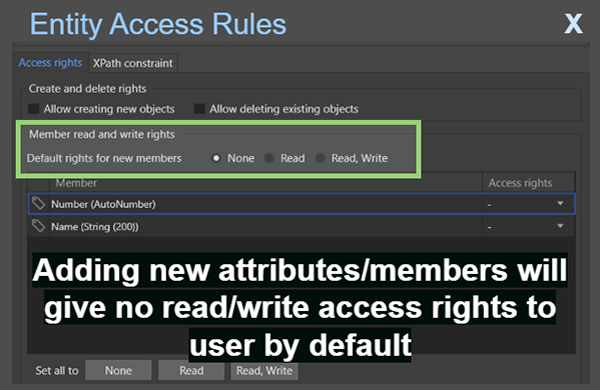
Whenever security isn’t granted, the default option should be to give the least access to resources. By denying access by default, application design errors are less likely to result in inappropriate permission to data. Mendix provides fail-safe defaults within entity access, where default rights to new entity attributes can be limited to no permissions for users. This means that when new attributes are added, developers need to explicitly grant users access rights to this data, reducing the risk to data confidentiality and integrity.
2. Least privilege
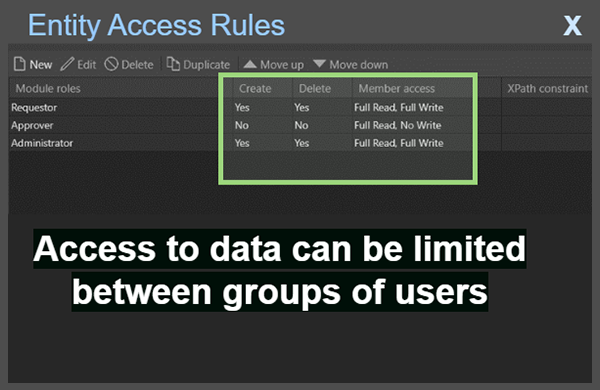
In 2022, IBM highlighted that 51% of organisations surveyed don’t use zero trust – a model that assumes users accessing resources cannot automatically be trusted. Using the principle of least privilege can help achieve the goals of the zero trust model. Each user should only have access to the resources they need to complete their tasks. Mendix’s security helps to implement the principle of least privilege in projects by assigning specific access to different user roles. This gives developers full control over what different users can access, ranging from page access through to member access within an entity.
3. Isolation
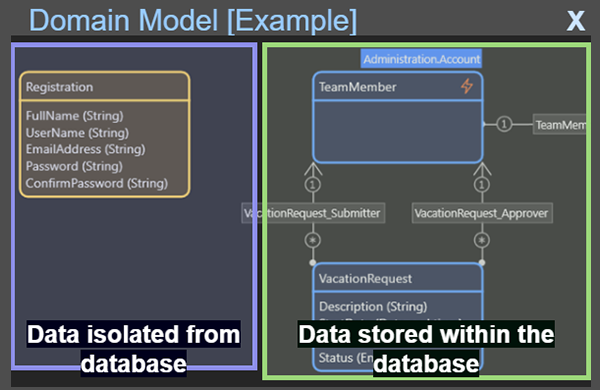
Public access systems should be isolated from critical resources, such as sensitive customer data. To help achieve isolation in Mendix, non-persistent entities help in public resources function without allowing anonymous users to access sensitive application data. For example, a registration form can use non-persistent entities to isolate anonymous users from the database, limiting any vulnerability to data breaches. This isolation of the database helps to reduce the risk of malicious users, as developers can restrict access to data until a user has achieved a minimum level of trust, such as logging into the application.
4. Layering
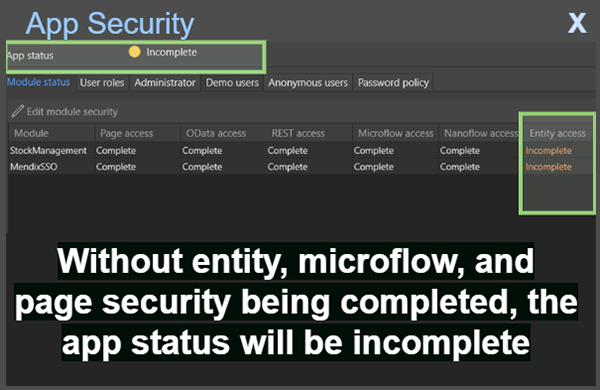
Relying on one mechanism of security can cause products to have a single point of failure; if that single security mechanism fails, the risk of unrestricted data access is increased. In Mendix, security needs to be implanted in three places before production is granted: domain model, microflows, and pages. This technique provides a depth of defences whereby if one fails, the product is unlikely to be compromised because of the other layers of security in place.
5. Compromise recording
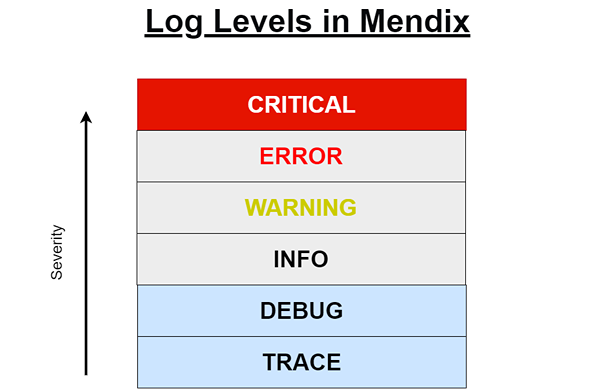
To prevent and detect intrusion, information needs to be recorded to assist in locating any suspicious activity. Mendix provides comprehensive logging management in projects that can assist in recording activity within a deployed application. These logging activities follow a hierarchical system, whereby unexpected behaviour can be identified through an increased severity in log level.
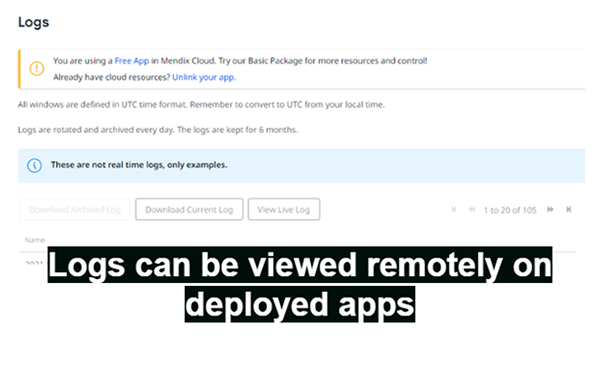
Alongside integrating log activities during project development, Mendix also provides the ability to view live logs on a deployed app. This can assist in compromise recording for a company, whereby unexpected actions from a user can be identified in real time.
Conclusion
In summary, Mendix provides multiple features in its platform to help prevent the unauthorised access of information from your database. These features come with a large range of flexibility – from defining security for the entire app, to access controls and individual attributes stored on your database. With these features visible throughout the platform, secure development can be a primary focus throughout an applications lifecycle.