AuraQ has vast experience helping organisations find the gaps that can be filled to enhance their business. This could be to improve efficiency, integrate legacy systems or deliver new portals and strategic applications to create competitive advantage. Contact us to request a free, no obligation Gap Analysis.
Perfect storm for cyber attacks – the importance of secure development
Question: What do you get when you mix an age where cyber crime is at an all-time high with a period where millions of people are having to work remotely from home due to a worldwide pandemic?
Answer: The perfect storm for cyber attacks and a very lucrative period for cyber criminals!
To put this into context, here are some interesting facts which demonstrate just how real this threat is for all organisations:
- The proportion of attacks targeting home workers increased from 12% of malicious email traffic before the UK’s lock-down began in March to more than 60% six weeks later (Darktrace)
- Almost half of businesses (46%) and a quarter of charities (26%) report having cyber security breaches or attacks in the last 12 months (Cyber Security Breaches Survey)
- Hackers attack every 39 seconds, on average 2,244 times a day (University of Maryland)
- The average time to identify a breach in 2019 was 7 months (IBM)
There really has never been a more critical time to re-evaluate your organisations Secure Development Policy. Here at AuraQ we have been doing just that.
What is secure development and why is it necessary?
A secure development policy contributes to the reliability of the IT environment by ensuring that as many vulnerabilities as possible are designed and tested out of software before it is transitioned into the live environment. It helps AuraQ provide assurance to both new and existing customers that software has been built not only to their requirements, but with consideration to cyber security at each stage of the software lifecycle; from design, development, testing and operation. Internally, the policy provides AuraQ’s staff with a set of principles to adhere to when developing software and a form of best practice guidelines which they can refer to. It ensures that our staff are up to date with the latest cyber security threats and we provide training to all staff members as to what’s new in the world of cyber security and what the latest developments are in cyber threats.
OWASP Foundation
Our policy and principles were written in conjunction with the resources available through the OWASP foundation. Open Web Application Security Project (OWASP) is an international non-profit organisation that educates software development teams on how to conceive, develop, acquire, operate and maintain applications so that they can be trusted. It provides many useful resources which we as a company have utilised to ensure that we are building software in a secure manner. Two of OWASP’s most utilised projects include:
OpenSAMM – OWAPS Project
The Open Software Assurance Maturity Model (OpenSAMM) is an open framework which helps organisations formulate and implement a strategy for software security that is tailored to the specific risks facing the organisation. The resources provided by OpenSAMM aid in:
- Evaluating an organisation’s existing software security practices.
- Building a balanced software security program in well-defined iterations.
- Demonstrating concrete improvements to a security assurance program.
- Defining and measuring security-related activities within an organisation.
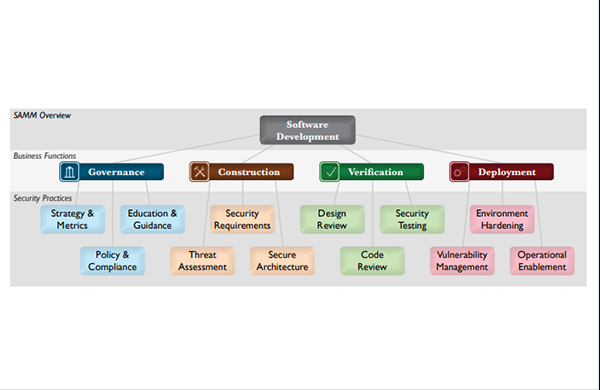
The main purpose of using SAMM is to build a software assurance model for an organisation. This process begins with the security assessment using the organisation existing model. After the assessment, Open SAMM proposes several road map templates to choose from. Organisations can further customise their road map based on these templates, which explains which section of security practice needs improvement and based on this, endeavour to achieve the required level. The foundation of the model is built upon the core business functions of software development with security practices tied to each. The objectives of the model are categorised into three maturity levels under each of the security practices. So, in total the model includes four business functions, 12 security practices, and 36 objectives. These objectives define a wide variety of activities in which an organisation could engage to reduce security risks and increase software assurance.
OWASP Top 10
The OWASP Top 10 is a regularly updated report outlining security concerns for web application security, focusing on the 10 most critical risks. The report is put together by a team of security experts from all over the world. OWASP refers to the Top 10 as an ‘awareness document’ and they recommend that all companies incorporate the report into their processes to minimise and/or mitigate security risks.
Summary
Organisations must ensure that the projects they deliver are safe and secure for both themselves as an organisation and also for their customers whom they trust to deliver safe and secure software products. This is just a brief outline of only two of the many OWASP projects available. There are over 50 OWASP projects online comprising of tools, documentation and code.
There is a wealth of information and resources online which can be utilised to achieve a strong security policy which works for your organisation no matter the size or industry.